Update: see mitmproxy.org for recent releases!
I spend a lot of time poking at web interfaces, both for penetration testing and generally while developing software. This usually involves iteratively making small modifications to requests, and running them again and again until I find a vulnerability or reproduce a bug. Using a browser plugin like tamperdata is great for a quick first stab at things, but gets clunky quickly. Scripting things up is usually the next step, and that's fine, but time-consuming and not very agile.
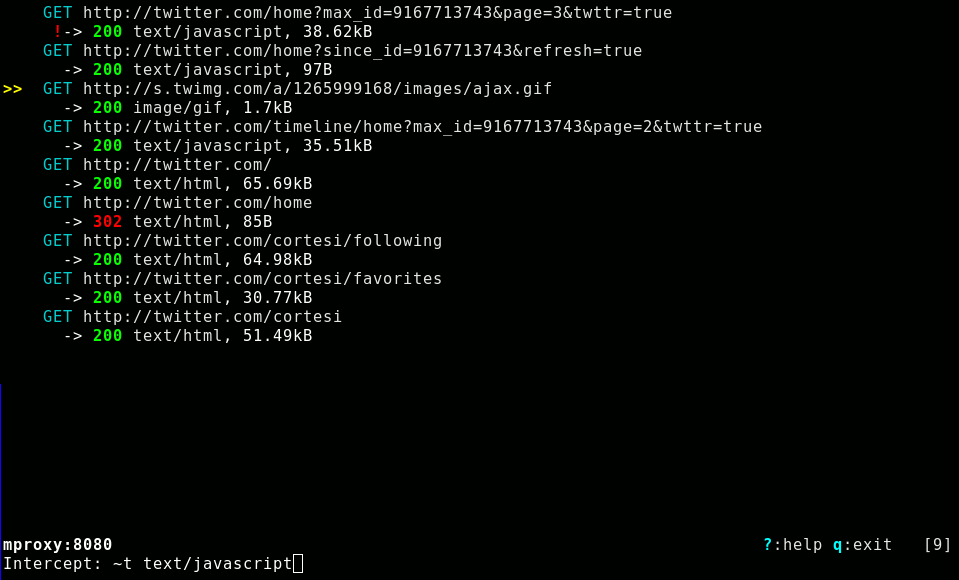
So, I'm releasing mitmproxy - an interactive, SSL-aware man-in-the-middle proxy that lets you view, modify and replay HTTP connections. It's aimed at software developers and penetration testers (i.e. people like me), who need to intensively tamper with and monitor HTTP traffic. Using it, you can point your browser at a page that loads a bazillion images and 50 snippets of JSON, pick out the one request you're interested in, and modify and replay it over and over. You have complete control over both requests and responses - you can edit headers and content using your preferred text editor, and change HTTP request methods on the fly. You can view request and response contents using an external viewer (picked using your mailcap configuration), or using mitmproxy's built in text and hexdump-like viewers. Filters and intercepts are specified using regular expressions and a pretty complete mutt-like expression language.
Another useful feature is something I call "sticky cookies". I often need to make requests using an authenticated session. This is a pain when logins are action. Copying cookie values around or scripting up the login process gets old quick. So, mitmproxy lets you set cookies on requests matching a specified expression as "sticky", which means that requests without a cookie inherit previously seen cookie values. So, you can log in to the target site once using your browser, and subsequent requests using tools like curl will automagically look like they're part of an authenticated session.
I've just sliced mitmproxy raw and quivering out of a much larger internal problems.
You can find releases and documentation for mitmproxy here. As usual, the real action is at the project's git repository.