I'm happy to announce the release of mitmproxy 0.8. This release has a few major new features, big speedups, and many, many small bugfixes and improvements. Here are the headlines:
Android interception
The most prominent new feature is that we now have a supported way to intercept Android traffic. What's more, we can do this without a cumbersome transparent proxying rig - see the Android section in the documentation for the details. Special thanks goes to Jim Cheetham for lending me an Android device and helping to get this feature off the ground.
Replacement patterns
Another exceedingly useful new feature is replacement patterns. These consist of a filter, a regular expression and a replacement string, and run continuously while mitmproxy processes requests and responses. You can pass these either on the command-line, or using a built-in replacement pattern editor.
I'm sure you can immediately think of many uses for this flexible feature, but my favourite is to use it during testing as a way to conveniently inject complicated exploits into web traffic. I do this by setting a replacement pattern that swaps a short but likely unique string (say MYXSS) for a long exploit, and then I use simple interaction and front-end tools like Firebug to inject exploits into requests manually based on the short string marker.
Improved pretty-printing of request and response contents
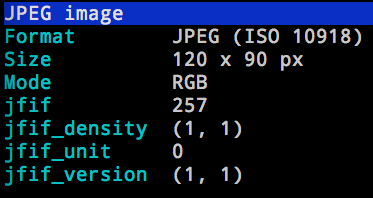
This release of mitmproxy has a completely redesigned subsystem for pretty-printing request and response bodies. For instance, we now extract EXIF tags and other basic information to give you something better than a hex dump when looking at an image:
We also have much improved HTML indenting (using lxml), and a built-in JavaScript beautifier (thanks to JSBeautifier) that teases out compressed and obfuscated scripts into something readable.
Changelog
- Detailed tutorial for Android interception. Some features that land in this release have finally made reliable Android interception possible.
- Upstream-cert mode, which uses information from the upstream server to generate interception certificates.
- Replacement patterns that let you easily do global replacements in flows matching filter patterns. Can be specified on the command-line, or edited interactively.
- Much more sophisticated and usable pretty printing of request bodies. Support for auto-indentation of JavaScript, inspection of image EXIF data, and more.
- Details view for flows, showing connection and SSL cert information (X keyboard shortcut).
- Server certificates are now stored and serialized in saved traffic for later analysis. This means that the 0.8 serialization format is NOT compatible with 0.7.
- Add a shortcut key ("f") to load the remainder of a request or response body, if it is abbreviated.
- Many other improvements, including bugfixes, and expanded scripting API, and more sophisticated certificate handling.