A few weeks ago, I posted that I had hacked up a version of mitmproxy that exploited CVE-2014-1266, giving unrestricted access to nearly all HTTPS traffic on affected IOS and OSX devices. I chose not to release working code at the time, but a number of POCs have been floating about publicly almost since the issue was first discovered. So, the time has come to publish - as of yesterday, mitmproxy's master branch supports #gotofail.
To see the exploit in action, invoke mitmproxy as follows:
mitmproxy --ciphers="DHE-RSA-AES256-SHA" --cert-forward
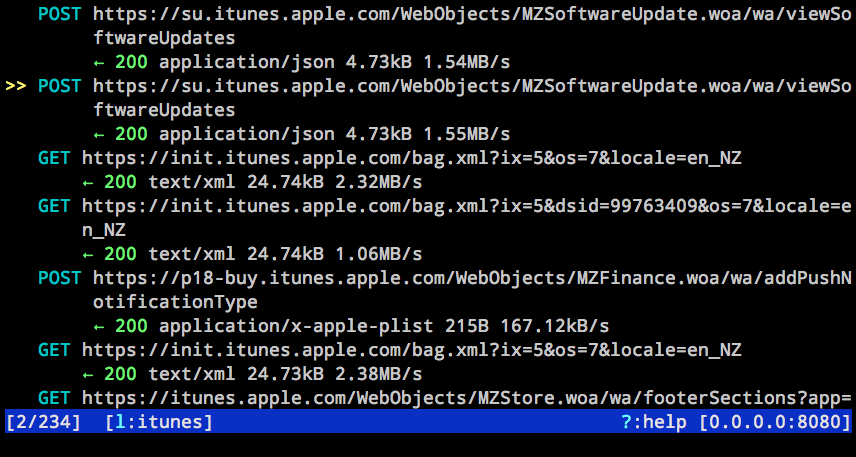
After configuring your device proxy, you should see something like this screenshot, which shows off interception of miscellaneous iTunes traffic:
Note that the client device here has no mitmproxy CA certificate installed, and we get circumvention of certificate pinning "for free".
Two new options make the magic work. The --ciphers option specifies which SSL ciphers we should expose to connecting clients. In this case, we force the client to use a DHE cipher, which is required to trigger the issue. The --cert-forward option tells mitmproxy to pass upstream SSL certificates down to the client unmodified. Usually we'd expect this to fail, since the upstream certs won't match mitmproxy's private key. In this case #gotofail means the client fails to properly execute the check, letting us pass certificates through to the client verbatim as if we owned them.
There's one additional wrinkle that mitmproxy smooths over - before we can get the mismatching certificate and key to the client, OpenSSL itself has to be coaxed into accepting them. The first version of my exploit involved a patch to OpenSSL to remove the library's own consistency check, but this is inconvenient. Luckily it turns out that we can munge an obscure flag in the RSA data-structures to circumvent this, which allows us to exploit #gotofail in pure Python.
The moment I got this exploit working, I marched upstairs and confiscated my wife's un-updated iPhone 5 to add it to my pool of test devices (never fear - it's been replaced with a nice new 5S). Devices running IOS of the right vintage have suddenly become the gold standard for analysis and pen testing. This beautiful vulnerability lets us circumvent SSL effortlessly, completely sidestepping certificate pinning for all the applications I've tried, without any cumbersome and invasive interference with the device. Combine this with the fact that these same devices also have an un-tethered jailbreak, and I think it's unlikely that we'll ever have an analysis platform this nice again. So, stockpile your IOS 7.0.6 devices now, and intercept all the things.